TORRANCE, Calif., Dec. 12, 2025 (GLOBE NEWSWIRE) — In December 2025, the critical React Server Components (RSC) vulnerability known as React2Shell (CVE-2025-55182) was publicly disclosed, revealing a structural flaw that enables unauthenticated remote code execution (RCE) across the React ecosystem. As active scanning and exploitation attempts rapidly followed and the vulnerability was added to CISA’s Known Exploited Vulnerabilities (KEV) catalog, understanding real-world exposure became an urgent priority for organizations worldwide. Criminal IP, AI SPERA’s cyber threat intelligence platform, analyzed global RSC-enabled services to assess the scale of risk, identify exposed assets, and monitor attacker activity—providing critical visibility into how React2Shell is impacting production environments and how organizations can respond effectively
React2Shell is not tied to a specific framework; rather, it stems from a structural weakness in the RSC feature that affects the broader React ecosystem. This article examines the technical foundation of React2Shell, the exposure landscape of services using RSC, observed attacker activity, and the defensive strategies organizations should adopt.
React2Shell Vulnerability Overview: A Structural Flaw Allowing RCE Without Authentication
CVE-2025-55182 is caused by a validation flaw in the deserialization process of the Flight protocol, which React Server Components use to exchange state between the server and client. An attacker can achieve RCE simply by sending a crafted payload to the Server Functions endpoint without authentication, and because a PoC is already publicly available, the vulnerability is highly susceptible to automated attacks.
The impact extends to all services that use RSC, and because frameworks such as Next.js, React Router RSC, Waku, Vite RSC Plugin, Parcel RSC Plugin, and RedwoodJS share the same underlying structure, the broader React ecosystem is collectively exposed.
The official patch is available in react-server-dom-* packages version 19.0.1 / 19.1.2 / 19.2.1 or later, and the vulnerability is rated CVSS 10.0, indicating critical severity.
Exposure Analysis of React2Shell-Affected Assets Using Criminal IP
React2Shell is difficult to detect using traditional product banners or HTML content alone. React-based services are designed so that RSC components are not externally exposed, and frameworks like Next.js, which vendor React modules internally, make it even harder to identify the underlying technology stack. As a result, simple banner-based detection methods cannot reliably determine whether RSC is enabled or whether a service is exposed to this vulnerability.
In real-world environments, the most reliable detection method is to identify systems based on their HTTP response headers, and servers with RSC enabled consistently exhibit the following values.
Criminal IP Search Query: “Vary: RSC, Next-Router-State-Tree”
Users can detect RSC-enabled servers in the United States using Criminal IP by applying queries based on these header patterns.
Criminal IP Search Query: “Vary: RSC, Next-Router-State-Tree” country: “US”
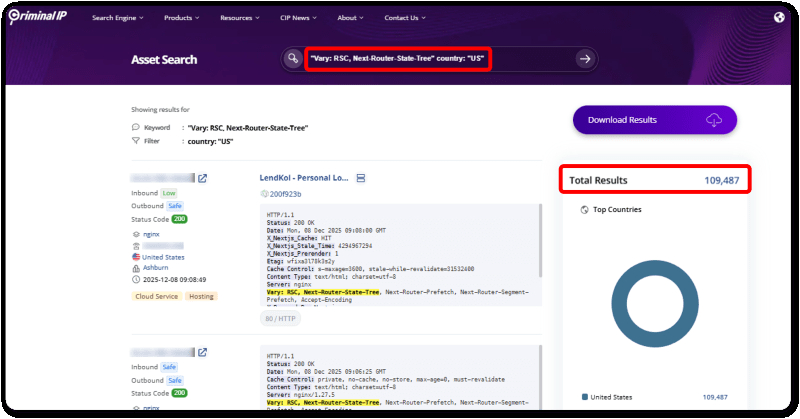
According to the Criminal IP Asset Search results, the query “Vary: RSC, Next-Router-State-Tree” country: “US” identified a total of 109,487 RSC-enabled assets. This header pattern indicates that RSC is active on these servers. While it does not mean that all of them are vulnerable, it is a critical indicator of the large-scale exposure surface that exists.
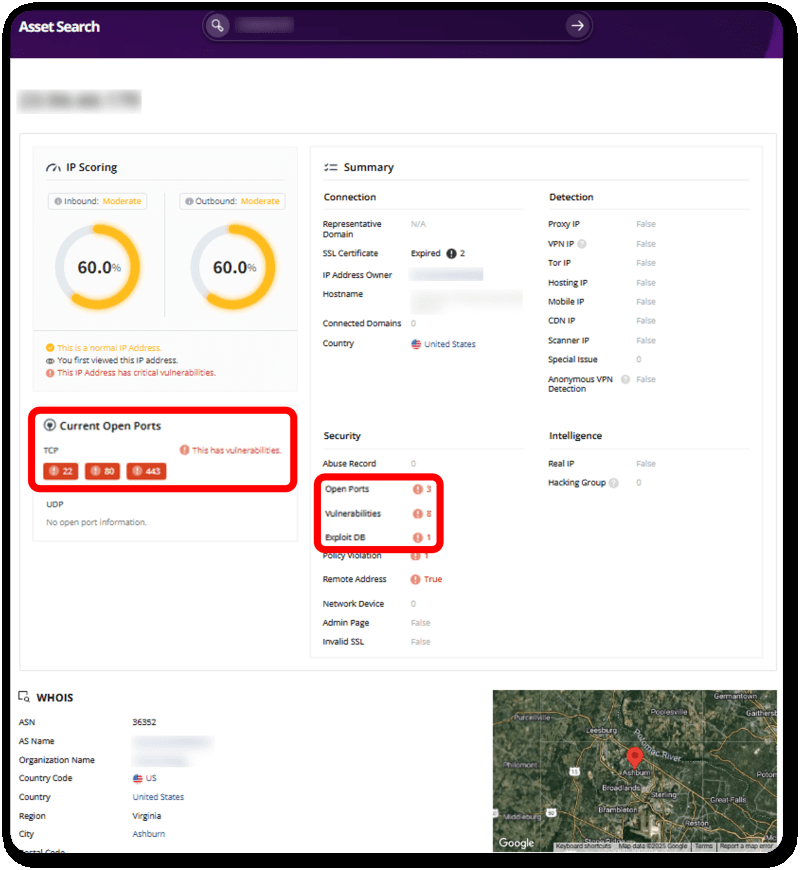
When examining the analysis results for a specific asset in Criminal IP, the server was found to have ports 80 and 443 exposed externally, and its response headers, SSL certificate details, vulnerability list, and Exploit DB associations could all be reviewed in a single unified page. In this asset, indicators relevant to React2Shell were identified alongside other critical vulnerabilities, including CVE-2023-44487 (HTTP/2 Rapid Reset), which has been widely abused in large-scale DDoS attacks.
This demonstrates how Criminal IP Asset Search provides multiple analysis layers that help assess whether an environment is realistically exploitable by attackers.
Security Mitigation Strategies
1. Immediate Update of React-Related Packages
Organizations should immediately update all React-related packages to their latest patched releases. The react-server-dom-webpack package must be upgraded to version 19.0.1, 19.1.2, or 19.2.1, while react-server-dom-parcel and react-server-dom-turbopack should be updated to version 19.0.1 or later to ensure they are protected from the vulnerability.
2. Verify Patch Availability for Each Framework
React RSC is used across multiple frameworks, including Next.js, Vite, Parcel, and RedwoodJS. Notably, Next.js vendors RSC internally, meaning that updating React packages alone may not automatically apply the fix. Therefore, it is essential to review each framework’s official security advisories or release notes and upgrade to the version in which the vulnerability has been addressed.
3. Minimize External Exposure of RSC Endpoints
Whenever possible, restrict access using a reverse proxy, WAF or authentication gateway.
4. Leverage Criminal IP for Monitoring
- Monitor exposure of RSC-related header
- Detect scanning attempts based on TLS fingerprints
- Automatically block malicious scanning IPs
- Check for vulnerability presence and associated Exploit DB entries
The Analysis’ Conclusion
React2Shell (CVE-2025-55182) is a critical vulnerability affecting the most widely used React-based services across the web ecosystem. With low exploitation complexity and publicly available PoCs, active attacks are spreading rapidly.
According to Criminal IP analysis, approximately 110,000 RSC-enabled services in the United States are exposed, underscoring the substantial risk of widespread exploitation. In addition to applying patches, identifying exposed RSC services and conducting real-time monitoring are essential components of an effective React2Shell response strategy. Criminal IP provides one of the most effective tools for accurately mapping this attack surface and strengthening defensive measures.
In relation to this, users can refer to Next.js Middleware Vulnerability Allows Authentication Bypass: Over 520K Assets at Risk.
About Criminal IP
Criminal IP is the flagship cyber threat intelligence platform developed by AI SPERA. The platform is used in more than 150 countries and provides comprehensive threat visibility through enterprise security solutions such as Criminal IP ASM and Criminal IP FDS.
Criminal IP continues to strengthen its global ecosystem through strategic partnerships with Cisco, VirusTotal and Quad9. The platform’s threat data is also available through major US data warehouse marketplaces including Amazon Web Services (AWS), Microsoft Azure and Snowflake. This expansion improves global access to high quality threat intelligence from Criminal IP.
Contact
Michael Sena
AI SPERA
[email protected]
Photos accompanying this announcement are available at
https://www.globenewswire.com/NewsRoom/AttachmentNg/0cb7fe71-829e-4981-b158-2ad54aff77f7
https://www.globenewswire.com/NewsRoom/AttachmentNg/d20f60c7-a268-4472-83fa-1fccde88993a
https://www.globenewswire.com/NewsRoom/AttachmentNg/ec62a656-527d-43fc-bf30-bf85ef28b814

